Announced by Bastille in 2016, MouseJack is still an open vulnerability affecting devices sold today.
In This Report
Introduction
MouseJack is a class of vulnerabilities that affects the vast majority of wireless, non-Bluetooth keyboards and mice. These peripherals are ‘connected’ to a host computer using a radio transceiver, commonly a small USB dongle. Since the connection is wireless, and mouse movements and keystrokes are sent over the air, it is possible to compromise a victim’s computer by transmitting specially-crafted radio signals using a device which costs as little as $15.
An attacker can launch the attack from up to 100 meters away. The attacker is able to take control of the target computer, without physically being in front of it, and type arbitrary text or send scripted commands. It is therefore possible to perform rapidly malicious activities without being detected. The MouseJack exploit centers around injecting unencrypted keystrokes into a target computer. Mouse movements are usually sent unencrypted, and keystrokes are often encrypted (to prevent eavesdropping what is being typed).
However the MouseJack vulnerability takes advantage of affected receiver dongles, and their associated software, allowing unencrypted keystrokes transmitted by an attacker to be passed on to the computer’s operating system as if the victim had legitimately typed them.

In order to prevent eavesdropping, most vendors encrypt the data being transmitted by wireless keyboards. The dongle knows the encryption key being used by the keyboard, so it is able to decrypt the data and see what key was pressed. Without knowing the encryption key, an attacker is unable to decrypt the data, so they are unable to see what is being typed.

Conversely, none of the mice that were tested encrypt their wireless communications. This means that there is no authentication mechanism, and the dongle is unable to distinguish between packets transmitted by a mouse, and those transmitted by an attacker. As a result, an attacker is able to pretend to be a mouse and transmit their own movement/click packets to a dongle.

Problems in the way the dongles process received packets make it possible for an attacker to transmit specially crafted packets which generate keypresses instead of mouse movement/clicks.
Frequently Asked Questions
What is MouseJack?

MouseJack is a class of vulnerabilities that affects the vast majority of wireless, non-Bluetooth keyboards and mice. These peripherals are ‘connected’ to a host computer using a radio transceiver, commonly a small USB dongle. Since the connection is wireless, and mouse movements and keystrokes are sent over the air, it is possible to compromise a victim’s computer by transmitting specially-crafted radio signals using a device which costs as little as $15.
An attacker can launch the attack from up to 100 meters away. The attacker is able to take control of the target computer, without physically being in front of it, and type arbitrary text or send scripted commands. It is therefore possible to perform rapidly malicious activities without being detected.
The MouseJack exploit centers around injecting unencrypted keystrokes into a target computer. Mouse movements are usually sent unencrypted, and keystrokes are often encrypted (to prevent eavesdropping what is being typed). However the MouseJack vulnerability takes advantage of affected receiver dongles, and their associated software, allowing unencrypted keystrokes transmitted by an attacker to be passed on to the computer’s operating system as if the victim had legitimately typed them.
The public advisories have been registered with CERT.

What are the potential dangers of MouseJack?
MouseJack is essentially a door to the host computer. MouseJack can be used to remotely take over a computer, insert malware, and potentially infiltrate a network. How can people find out if their device is at risk? View a full list of affected devices.
Who discovered MouseJack?
Marc Newlin, a member of Bastille’s Threat Research Team. Bastille’s research team is made up of RF and cybersecurity experts including the top 4 finalists of the DARPA Spectrum Challenge.
What does the MouseJack discovery say about the current state of IoT security?
The MouseJack discovery validates the thesis that the IoT is being rolled out with wireless protocols that have not been through sufficient security vetting.
Who is at risk of being targeted by the MouseJack vulnerability?
From global enterprises to individuals, anyone using an affected wireless mouse runs the risk of being a victim of a potential hack.
Is there a MouseJack fix? What can consumers do to protect themselves?
A MouseJack fix is the responsibility of the device manufacturers. Consumers should check with their vendors to see if a fix exists. If a fix does not exist, consumers should consider replacing their device with a secure one. Find the list of affected devices here.
I have a Bluetooth keyboard/mouse. Am I vulnerable?
Not from MouseJack. Bluetooth uses a completely different transmission and encryption system that is not vulnerable to this attack.
How long does it take to hack my laptop with MouseJack?
A MouseJack compromise can take place in seconds. Don’t think of an attacker needing to use your keyboard/mouse for minutes looking through your interesting emails. In around ten seconds, your computer can be altered to allow an attacker to remotely download documents, all your emails, and add or delete programs.
Why would anyone care about attacking me on my laptop?
There are two plausible scenarios:
PERSONAL ATTACK: Identity theft is an increasing problem that can result in a negative credit rating and expensive legal battle to reclaim what is rightfully yours. Criminals are becoming increasingly sophisticated in how they piece together the necessary information to pretend to be you.
COMPANY ATTACK: Once your laptop is ‘MouseJacked’, malicious software can be installed that will remain dormant until you connect to your corporate network. The software will attempt to replicate across the rest of the computers connected to that network, exfiltrating sensitive documents and user credentials — this is modern corporate espionage.
Where is my laptop vulnerable?
Your laptop can be ‘MouseJacked’ from up to 100 metres away. You could be in the office and a visitor hacks you from reception, you could be at home and a hacker attacks you from the street, you could be in a coffee shop and another customer hacks you. The same threat exists at an airport, or on a plane, or in many other situations.
Bottom line
If your computer is turned on, and a vulnerable dongle is attached, it could be vulnerable to MouseJack.
Affected Devices
The following devices have been tested and are vulnerable to a MouseJack keystroke injection attack (specifically vulnerabilities that pertain to Bastille Threat Research Team Tracking Number #1-7, 9 & 12). To help determine whether you have an affected device connected to your system, please compare the following screenshots against your computer. Hardware information screens are provided for Windows, OS X and Linux for each USB dongle:
| Vendor | Affected Devices | Advisory | Vendor Response | USB ID Screenshots |
|---|---|---|---|---|
| AmazonBasics | Wireless Mouse MG-0975 USB dongle RG-0976 (USB ID 04f2:0976)) | #7 HID Packet Injection | ||
| Dell | Dell KM714 Wireless Keyboard and Mouse Combo KM714 USB dongle (USB ID 046d:c52b) KM632 Wireless Mouse USB dongle (USB ID 413c:2501) | #1 Force Pairing #2 Keystroke Injection #3 Fake Mouse #7 HID Packet Injection #11 Unencrypted Keystroke Injection Fix Bypass | Statement | |
| Gigabyte | K7600 wireless keyboardUSB dongle (USB ID 04b4:0060) | #6 Packet Injection | ||
| HP | Wireless Elite v2 keyboardElite USB dongle (USB ID 03f0:d407) | #5 HID Packet Injection | ||
| Lenovo | 500 Wireless Mouse (MS-436)500 USB Dongle (USB ID 17ef:6071) | #9 HID Packet Injection | LEN-4292 | |
| Logitech | K360K400rK750K830Unifying dongle (USB ID 046d:c52b)Tested firmware versions:012.001.00019012.003.00025 | #1 Force Pairing#2 Keystroke Injection#3 Fake Mouse | Firmware Update(With above update, #1, #2 & #3 are solved.) | |
| Logitech (update) | K400rLogitech Unifying Dongles C-U0007 (FW ver 012.005.00028) & C-U0008 (FW ver 024.003.00027) (both USB ID 046d:c52b)Logitech G900Logitech G900 dongle C-U0008 (USB ID 046d:c539) | #11 Unencrypted Keystroke Injection Fix Bypass#12 Unencrypted Keystroke Injection#16 Malicious Macro ProgrammingPlease note: these products also affected by KeyJack. | Firmware Update(With above update, #11 & #12 are solved.) | |
| Microsoft | Sculpt Ergonomic mouseWireless Mobile Mouse 4000Microsoft Wireless Mouse 50002.4GHz Transceiver v7.0 (USB ID 045e:0745)USB dongle model 1496 (USB ID 045e:07b2)USB dongle model 1461 (USB ID 045e:07a5) | #4 HID Packet Injection | 3152550Note: Mice part of a combo set are still vulnerable. | |
Note: links were updated in 2016 at time of discovery—vendors may change links without alerting us
Also covered in our advisories is a Denial-Of-Service vulnerability (Bastille Threat Research Team Tracking Number #8), which affects the following hardware:
| Vendor | Affected Devices | Advisory (with Tracking #) |
|---|---|---|
| Lenovo | N700 MouseN700 USB dongle (USB ID 17ef:6060)Ultraslim KeyboardUltraslim MouseUltraslim USB dongle (USB ID 17ef:6032)Ultraslim Plus KeyboardUltraslim Plus MouseUltraslim Plus USB dongle (USB ID 17ef:6022) | #8 Denial-Of-Service |
Although the Bastille Threat Research Team endeavored to test a wide variety of models of wireless keyboard and mice from multiple vendors, it is not possible to acquire and test every model available on the market. There may be other models and vendors that are affected by this class of vulnerability, so the list should not be considered definitive.
Public Advisories
The plain-text advisories can be found above, and at CERT/CC VU#981271
Remediation
If you’ve been affected by MouseJack use the following steps immediately:
- Immediately disconnect all affected USB dongles, and use wired keyboards and mice instead.
- If you are using affected Logitech or ‘Lenovo 500’ devices, please update your firmware by referring to the appropriate instructions (see appropriate Vendor Response links above).
Dongles from other vendors were not found to support upgrading of firmware, so it does not appear possible to patch them. Therefore it is recommended that users contact their preferred vendor and inquire into which models are not vulnerable for future purchases.
Helpful Tools
The Bastille Threat Research Team is releasing free, open source tools to enable interested parties to discover wireless mice and keyboards that may be vulnerable to MouseJack.
Refer to https://github.com/BastilleResearch/mousejack.
A Python-based sniffer is available, and will output raw frames to the console:

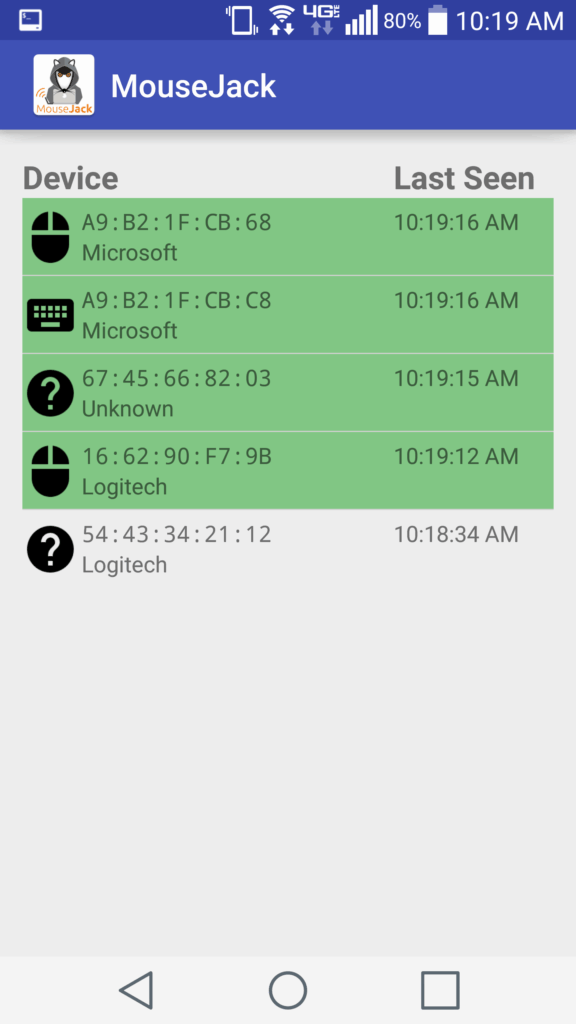
An Android application for sniffing has been developed and is now available:
Timeline
| Date | Events |
|---|---|
| 2015 November 24th | Initial vendor disclosure |
| 2016 January 11th | CERT/CC advisory sent |
| 2016 February 23rd | Public disclosure |
| 2016 February 24th | CERT/CC releases advisoriesAdded Logitech & Lenovo firmware update links |
| 2016 February 25th | Uploaded statement from Dell |


